Create access policies and tokens
You can manage Grafana Cloud Access Policies using one of the following methods:
- The Access Policies page in the Cloud Portal
- The Grafana Administration settings (Administration -> Users and access -> Cloud access policies)
- The Cloud Access Policy API. For API instructions, refer to the Access Policy section of the Grafana Cloud API document).
Required roles
To manage access policies from the Grafana Administration settings, you must have the Admin role within that Grafana (or another role that contains the grafana-auth-app:write permission). However, to manage access policies in the Cloud Portal, you must have the Admin role within the Cloud Portal. These roles are set independently.
Best practices
Following the principle of least privilege, an access policy should only have the necessary scopes. It’s better to create a specific access policy for a specific task, rather than create a single over-privileged access policy and use it for multiple tasks.
For example, since writing metrics is done separately from reading metrics, consider having:
- One access policy to read metrics
- One access policy to write metrics
Create an access policy for a stack
Stack access policies only work for a specific stack and can be used to read and write data. For example, a stack access policy could be used to read and write metrics, logs, and other related data for a single stack.
To create an access policy using Cloud access policies:
Sign in to Grafana Cloud and start the stack where you wish to create the access policy.
Click Administration in the left-side menu and select Cloud access policies.
Click Create access policy.
Enter a Display Name for the access policy.
Optional: Update the Name field. This field is automatically populated with the Display name.
Select one or more scopes for the policy. Not all scopes are displayed by default. If you do not see the scope that you are looking for, (for example,
stack:read) use the Add scope drop-down towards the bottom of the dialog, and select the scope you would like to configure.Add Label selectors, if desired. The label selectors use Prometheus labels. You can use operators like
!=and=.
Tip: Refer to Using label-based access control for additional information.Add IP ranges, if desired.
For more information, refer to Using IP range based access control with access policies.
Select Create to add the access policy.
Create an access policy for an organization or multiple stacks
Organization access policies work for all stacks within an organization and can be used to read and write data to any stack within the organization. An access policy can also be created for multiple specific stacks. Organization access policies can also be used for the Grafana Cloud API endpoints
To create an access policy using the organization’s Access Policies page:
Sign in to Grafana Cloud.
Select an organization in the drop-down at the top of the page.
Locate Security in the left-hand navigation and select Access Policies.
Select Create access policy.
Enter a Display Name for the access policy.
Optional: Update the Name field. This field is automatically populated with the Display name.
Optional: From the Realm drop-down select the organization (all stacks), or select one or more stacks.
Select one or more scopes for the policy.
Add Label selectors, if desired. The label selectors use Prometheus labels. You can use operators like
!=and=.
Tip: Refer to Using label-based access control for additional information.Add IP ranges, if desired.
For more information, refer to Using IP range based access control with access policies.
Select Create to add the access policy.
Note
When creating an access policy for the entire organization (all stacks) in the Cloud Portal, the policy is created in the “GCP US Central” region. If you need to create an organization-wide access policy in a different region, you can use the Cloud Access Policy API or Terraform provider.
Create tokens for an access policy
Tokens are the actual secret used to authenticate an action. Token permissions are controlled by the access policy they belong to. Specific usage of a token can be found here: Using an access policy token.
Note
The token is only shown once. Copy and save it in a safe place, like a secure note, password app, or other protected location.
To create a token for an access policy:
- Sign in to Grafana Cloud.
- Navigate to the access policies page.
- From within a Grafana Stack: Click Administration and select Cloud access policies.
- Using the Cloud Portal: Select your organization, then under Security, select Access Policies.
- Choose an access policy.
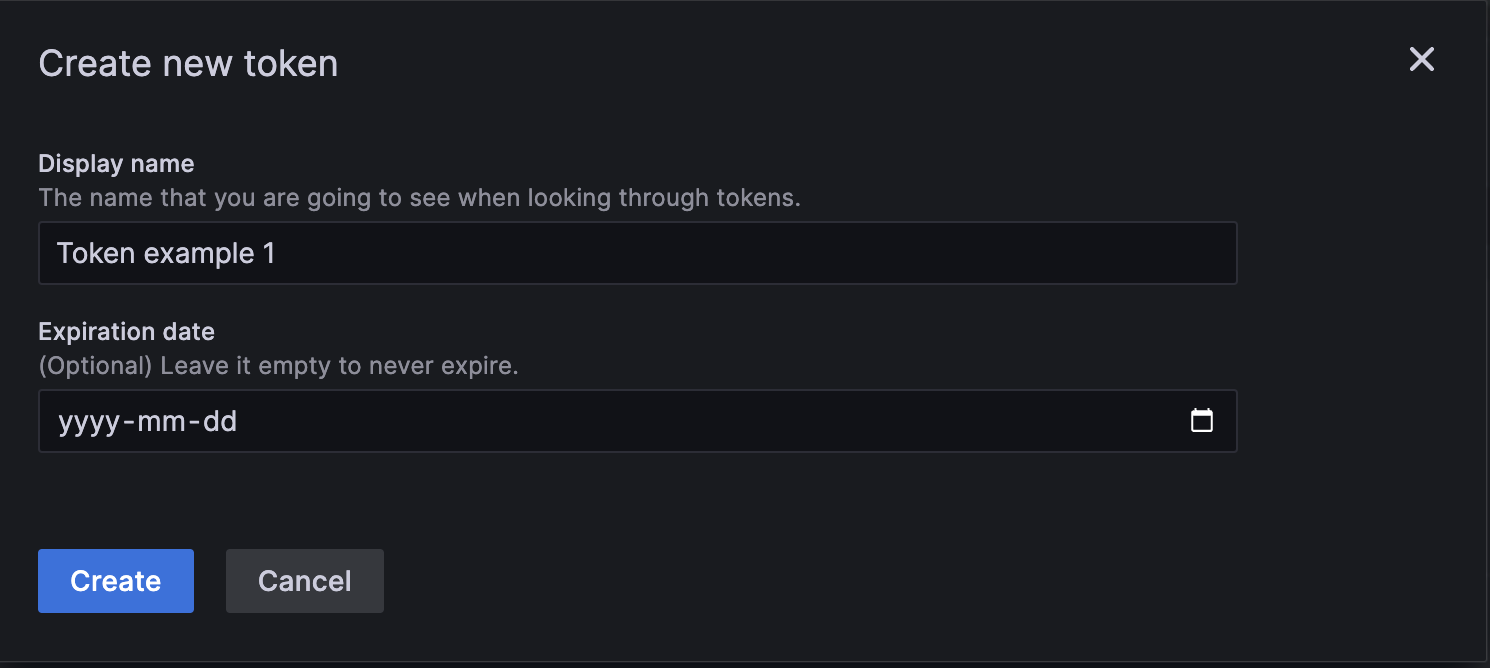
- Select Add token to display the Create new token dialog.
![Create a new token dialog Create a new token dialog]()
Create a new token dialog - Enter a Display name for the token.
- Optional: Enter an Expiration date in year/month/day format. Leave the field blank to prevent the token from expiring.
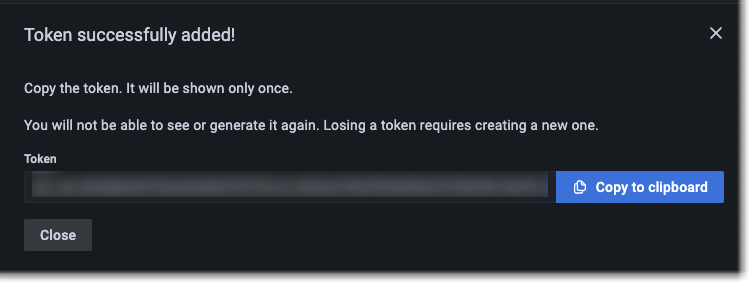
- Select Create to generate the token.
![The available scopes in the Cloud Access Policies plugin. The available scopes in the Cloud Access Policies plugin.]()
The available scopes in the Cloud Access Policies plugin. - Select Copy to clipboard to copy the generated token.
Modify an access policy
You can modify an access policy from the same UI where it was created. All access policies can be modified from the Access Policy page in the Cloud Portal or using the Cloud Access Policy API, but the only access policies that can be modified from the Grafana Administration settings are access policies specific to that stack (meaning they have a single stack realm).
To modify an access policy:
- Sign in to Grafana Cloud.
- Navigate to the access policies page.
- From within a Grafana Stack: Click Administration and select Cloud access policies.
- Using the Cloud Portal: Select your organization, then under Security, select Access Policies.
- Locate and select the access policy you wish to modify.
- Modify the policy as desired and select Update to save the changes.
Delete an access policy token
Once a token has been created, it can not be modified. Deleting a token will make it stop working. There may be a few minutes delay to apply everywhere.
To delete a token:
- Sign in to Grafana Cloud.
- Navigate to the access policies page.
- From within a Grafana Stack: Click Administration and select Cloud access policies.
- Using the Cloud Portal: Select your organization, then under Security, select Access Policies.
- Locate the access policy associated with the token you wish to remove.
- Select the trash can icon to the right side to remove the token.
- Confirm the removal by selecting Delete on the Delete token dialog.
Delete an access policy
Deleting an access policy removes all tokens associated with it. There may be a few minutes delay to apply everywhere.
To delete an access policy:
- Sign in to Grafana Cloud.
- Navigate to the access policies page.
- From within a Grafana Stack: Click Administration and select Cloud access policies.
- Using the Cloud Portal: Select your organization, then under Security, select Access Policies.
- Locate the access policy you wish to remove.
- Select the trash can icon to the right side to remove the policy.
- Confirm the removal by selecting Delete on the dialog.