How to query private network data without an agent using AWS and Grafana Cloud
Note: As of August 2025, the private preview for this feature — which let Grafana Cloud users establish a private connection using AWS PrivateLink and Amazon VPC Lattice without having to deploy the Private Data Source Connect (PDC) agent within their AWS environment — has ended. We have no current plans to develop it further. Instead, we recommend using the PDC agent-based approach, which is detailed in our documentation.
Connecting to data sources in a private network or an Amazon Virtual Private Cloud (Amazon VPC) can require extra attention to the network security configuration to prevent unintended network exposure. For example, if you wanted to query a network-secured data source, like a MySQL database or an Elasticsearch cluster, that is hosted in an on-premises private network, you would need to open your network to inbound queries from a range of IP addresses.
Luckily there are tools to help protect against those vulnerabilities. You can query your network-secured data sources from Grafana Cloud using Private Data Source Connect (PDC), which we rolled out last year to all tiers of Grafana Cloud. And if you want to build secure and efficient integrations between your AWS VPC resources and Grafana Cloud, that process just got much easier.
PDC can now establish a private connection using AWS PrivateLink and Amazon VPC Lattice, bypassing the public internet and eliminating the need to deploy the PDC agent within an AWS environment.
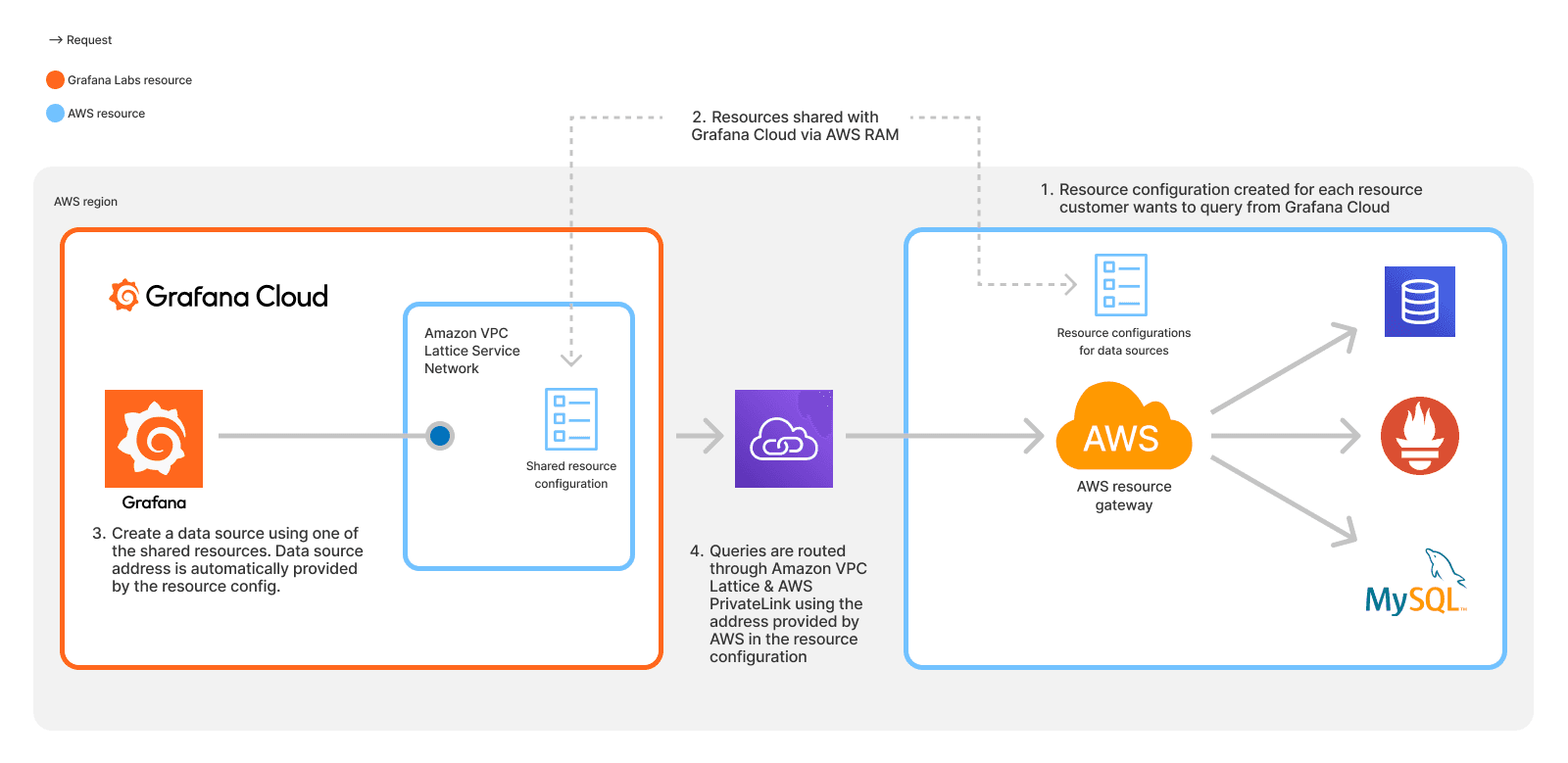
This new feature — which was announced at AWS re:Invent and is now available in private preview — means that your teams no longer need to allowlist a wide range of IP addresses. Instead, you can query and alert on your data securely within the AWS network, minimizing exposure to external threats while adhering to compliance standards across industries. You’ll also be able to quickly and more easily visualize and alert on your private data using the Grafana dashboards you know and love.
Key features and benefits
1. Granular control: Share resources with your Grafana Cloud stack, which will then be available to use as Grafana data sources. All queries to those resources will go over AWS PrivateLink. Access to these shared resources is completely within your control — you can remove access at any time.
2. Enhanced security: Using AWS PrivateLink and VPC Lattice, data flows through a secure, private network, reducing the risk of data interception and ensuring compliance with regulations like GDPR and HIPAA.
3. Optimized performance: AWS PrivateLink’s reliable, low-latency pathways result in improved responsiveness and efficiency of your Grafana dashboards, enhancing the overall user experience.
4. Ease of integration: PDC in Grafana Cloud simplifies the process of connecting AWS-hosted data sources, eliminating the need for complex VPN configurations and providing a straightforward setup process.
5. Cost effective: All transactions stay in your AWS network, eliminating the egress cost of sending your data through the public internet.
The combination of PDC with AWS PrivateLink and VPC Lattice is especially well-suited for industries where data security and integrity are critical:
- Financial services: Gain insights from financial data while safeguarding against unauthorized access.
- Healthcare: Monitor and evaluate health metrics with full compliance and data protection assurances.
- Technology and SaaS: Optimize infrastructure performance with secure, real-time monitoring capabilities.
Learn more about PDC in Grafana Cloud and AWS PrivateLink
This functionality in PDC using AWS PrivateLink and VPC Lattice is currently available in private preview. If you are interested in learning more,please contact the Grafana Labs team.
To learn more about PDC, check out our Private Data Source Connect documentation. For more on AWS offerings, check out the AWS PrivateLink documentation and the Amazon VPC Lattice web page.