Connect the PDC agent via GCP Private Service Connect
GCP Private Service Connect (PSC) provides private connectivity between private networks and supported GCP services without exposing your traffic to the public internet.
With GCP Private Service Connect for Private data source connect, you can connect your PDC agents running in your GCP private network to Grafana Cloud while staying on the GCP network.
By connecting your PDC agents via GCP Private Service Connect, you avoid traversing the public internet. This has security benefits and helps lower your network egress costs.
Before you begin
To use GCP Private Service Connect, you need the following:
- A Grafana Cloud stack hosted on GCP. Check where your stack is hosted by navigating to it in the My Account section of Grafana.com and clicking on Details for your Grafana service. If the region matches one of the GCP regions where Grafana Cloud is hosted, your stack is hosted on GCP.
Note
If your stack is not hosted on GCP, you must create a new stack hosted on GCP.
- A GCP network in which to create the private endpoints for your PDC agent.
Other regions
Grafana Cloud’s GCP PSC integration supports native cross-region connectivity, so you can connect to services hosted in other GCP Regions over PSC endpoints.
To set up cross-region connectivity, enable Global Access during PSC endpoint creation.
Set up Private Endpoints
You can create a Private Endpoint in the GCP console, or provision one using Terraform.
PDC requires the creation of two Private Endpoints: one for the API and another for the SSH gateway.
With the GCP Console
Open your GCP Console and navigate to Private Service Connect.
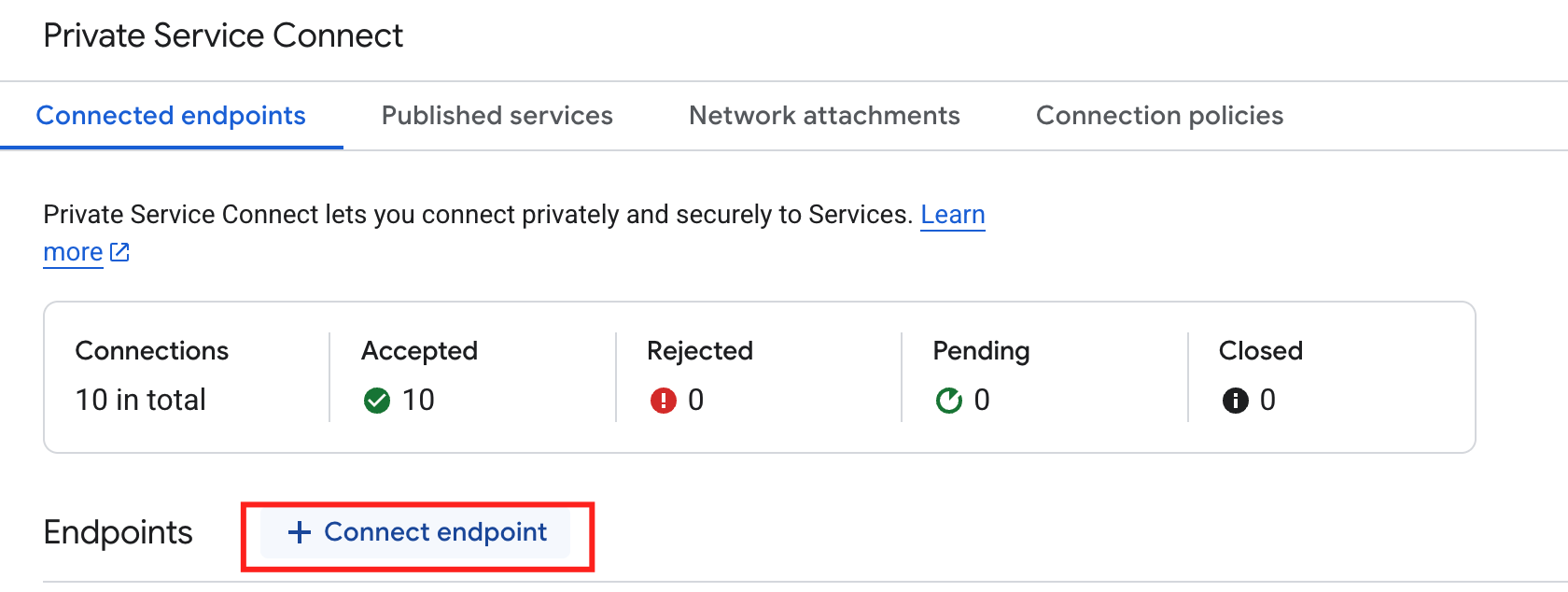
Click the Connected endpoints tab.
Click Connect endpoint.
![Connect endpoints]()
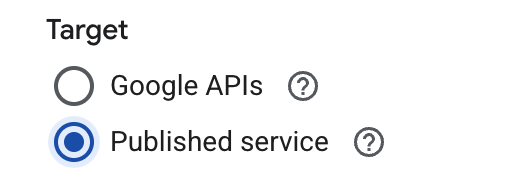
For Target, select Published service.
![Select target type]()
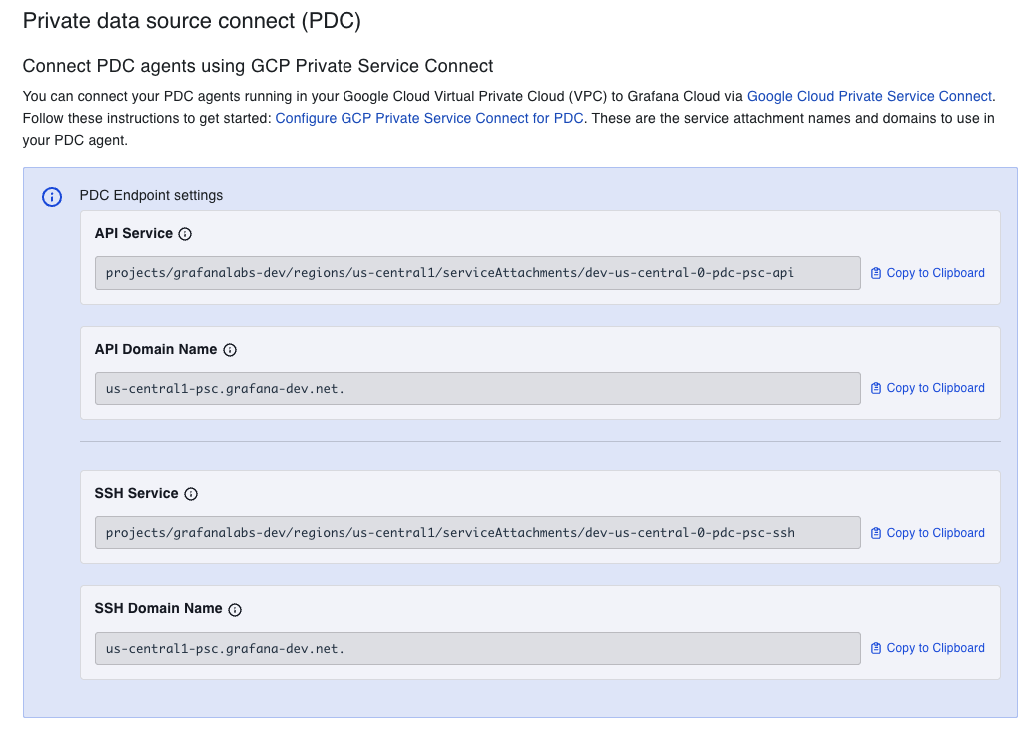
For Target service, enter the service attachment URI for the API from your Grafana Cloud stack. The service attachment URI is in this format:
projects/SERVICE_PROJECT/regions/REGION/serviceAttachments/NAMENavigate to your Grafana Cloud account, select your stack, and click Details for the Grafana service. Under the header “Connect PDC Agents using GCP Private Service Connect”, copy the API Service field.
![Find Service Attachment URI]()
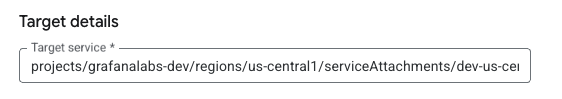
Enter provided value for the API into the Target service field in the GCP console.
![Enter Service Attachment URI]()
For Endpoint name, enter a name to use for the endpoint, for example
pdc-api. Note this is also the name for the DNS record.![Enter Endpoint name]()
Select a Network and Subnetwork for the endpoint.
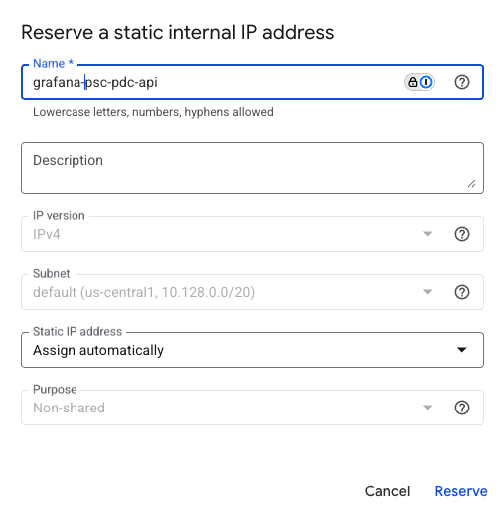
Select an IP address for the endpoint. If you need a new IP address, you can create one:
- Click the IP address drop-down menu and select Create IP address.
- Enter a Name and optional Description for the IP address. For example, as name you can use
grafana-psc-pdc-api - Select Assign automatically or Let me choose.
- If you selected Let me choose, enter the Custom IP address you want to use.
- Click Reserve.
![Create IP Address]()
To make the endpoint available from any region, select Enable global access. If you do not plan to use cross-region connectivity, you can leave this option disabled.
![Enable Global access]()
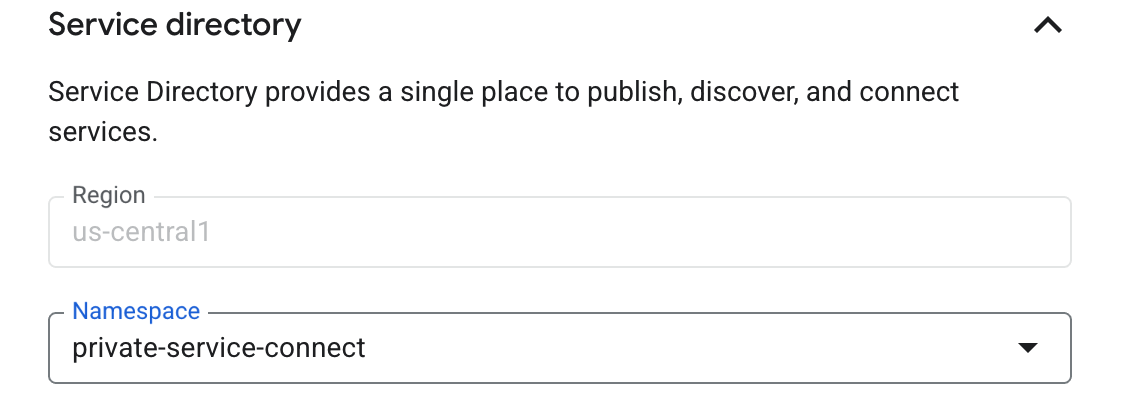
Open the Service Directory option and select a Namespace from the drop-down list; or, create a new namespace for the region. The Region is populated based on the selected
subnetwork. Service Discovery configures a Private DNS zone for<region>-psc.grafana.netand create records for the endpoint, in this examplepdc-api.us-central1-psc.grafana.net.![Configure Service Discovery]()
Click Add endpoint.
The new PSC endpoint is being created.
![Waiting for endpoint to be create]()
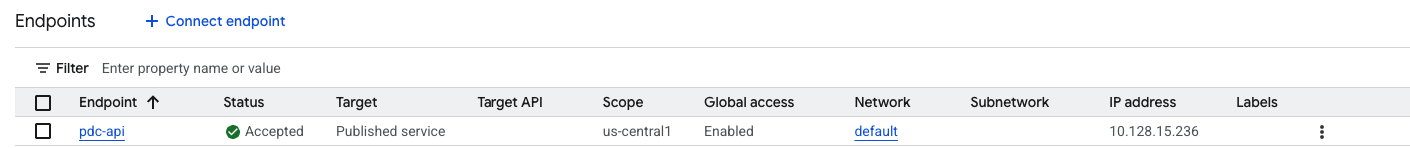
After a short period of time, the endpoint is created and status is set to
Available.![An endpoint with Status: “Available”]()
Repeat this PSC Endpoint creation process now for the PDC SSH Gateway. In this case, it is mandatory the Endpoint name is set to
private-datasource-connect. Therefore, the DNS record created isprivate-datasource-connect.us-central1-psc.grafana.net.Configure your PDC agent to use the DNS names for the Private Endpoints. Use these values for the
-api.fqdnand-gateway.fqdnflags respectively. You can remove the-clusterflag. Following is an example configuration:./pdc \ -api-fqdn pdc-api.us-central1-psc.grafana.net \ -gateway-fqdn private-datasource-connect.us-central1-psc.grafana.net \ -token <token> \ -gcloud-hosted-grafana-id <id>
With Terraform
Use the following snippet to automate PSC Endpoint setup in GCP using Terraform:
locals {
network_id = "<your-network-id. eg. `default`>"
subnetwork_id = "<your-subnetwork-id. eg. `default`>"
service_discovery_namespace = "<your-sd-namespace-id. eg `private-service-connect`>"
endpoint_name_api = "pdc-api"
grafana_service_api = "<API Service Name provided by Grafana. eg `projects/grafana-test/regions/us-central1/serviceAttachments/psc-pdc-api`>"
endpoint_name_ssh = "private-datasource-connect"
grafana_service_ssh = "<SSH Service Name provided by Grafana. eg `projects/grafana-test/regions/us-central1/serviceAttachments/psc-pdc-ssh`>"
grafana_service_region = "<GCP region where Grafana service is available. eg. `us-central1`>"
}
# IP Address
resource "google_compute_address" "psc_pdc_api" {
name = local.endpoint_name_api
region = local.grafana_service_region
subnetwork = local.subnetwork_id
address_type = "INTERNAL"
}
resource "google_compute_address" "psc_pdc_ssh" {
name = local.endpoint_name_ssh
region = local.grafana_service_region
subnetwork = local.subnetwork_id
address_type = "INTERNAL"
}
resource "google_compute_forwarding_rule" "psc_pdc_api" {
name = local.endpoint_name_api
region = local.grafana_service_region
load_balancing_scheme = "" # Explicit empty string required for PSC
target = local.grafana_service_api
network = local.network_id
subnetwork = local.subnetwork_id
ip_address = google_compute_address.psc_pdc_api.id
allow_psc_global_access = true
service_directory_registrations {
namespace = local.service_discovery_namespace
}
}
resource "google_compute_forwarding_rule" "psc_pdc_ssh" {
name = local.endpoint_name_ssh
region = local.grafana_service_region
load_balancing_scheme = "" # Explicit empty string required for PSC
target = local.grafana_service_ssh
network = local.network_id
subnetwork = local.subnetwork_id
ip_address = google_compute_address.psc_pdc_ssh.id
allow_psc_global_access = true
service_directory_registrations {
namespace = local.service_discovery_namespace
}
}