Configure Azure Private Link
Send telemetry data from your Azure Virtual Network to Grafana Cloud via Azure Private Link in order to:
- Reduce your Azure egress costs.
- Improve security by keeping your data within the Azure network.
To use this feature, configure a Private Endpoint in your Azure Virtual Network. Your local agents can use this endpoint to route data to Grafana Cloud via Azure Private Link.
Prerequisites
To use Azure Private Link, you need a Grafana Cloud stack hosted on Azure and an Azure Virtual Network.
Grafana Cloud stack on Azure
To check where your stack is hosted, navigate to your account in Grafana Cloud, and click Details for a given service, such as Prometheus or Loki.
If the region matches one of the Azure regions where Grafana Cloud is hosted, then your stack is hosted on Azure.
If your stack is not hosted on Azure, create a new stack, forward telemetry to it, and query it from your existing stack.
Azure Virtual Network
On the Azure Virtual Network, create a private endpoint to forward your telemetry data.
Other regions
Azure Private Link supports cross-regional connections. If your infrastructure is hosted in a different Azure region than the one where Grafana is hosted, you can still benefit from Private Link.
Set up a Private Endpoint
Create a Private Endpoint in the Azure console, or provision one using Terraform.
Use the Azure Console
Open your Azure Console and navigate to Private Endpoints.
![Select Private Endpoint > Endpoints]()
Choose Create.
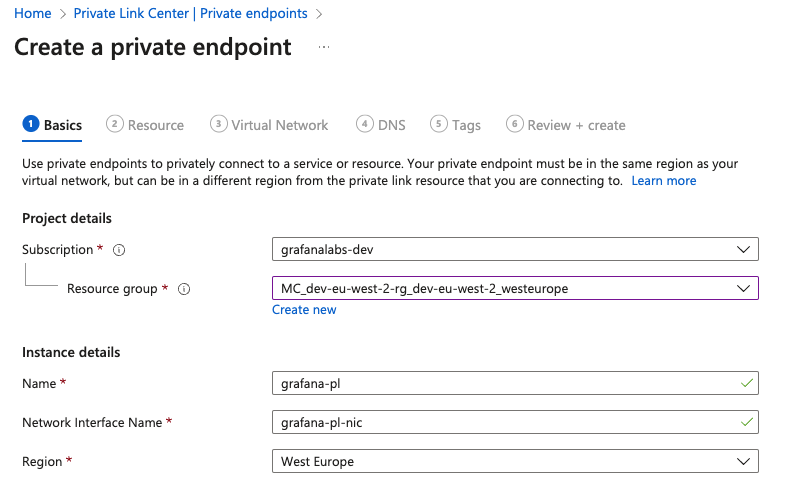
Select the subscription and resource group where your virtual network is.
Give the endpoint a name, for example,
grafana-pl.![Enter name]()
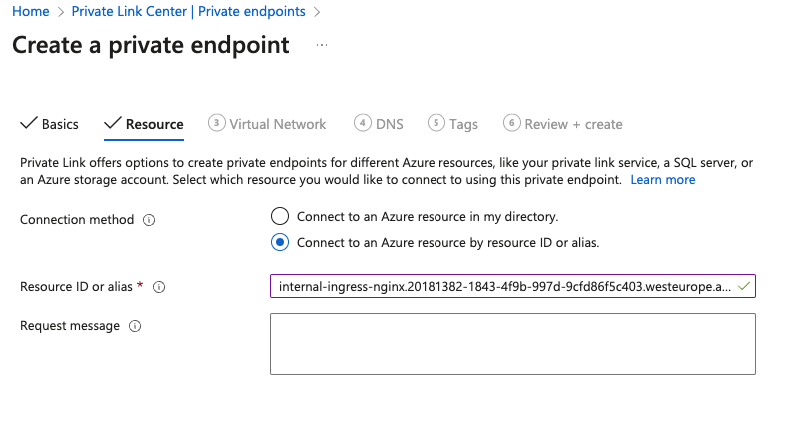
Continue to the Resource tab and select Connect to an Azure resource by resource ID or alias.
In the Resource ID or alias field, enter the service alias from your Grafana Cloud stack.
![Select service]()
In the Request Message field, add some text for future reference, like your Grafana organization name.
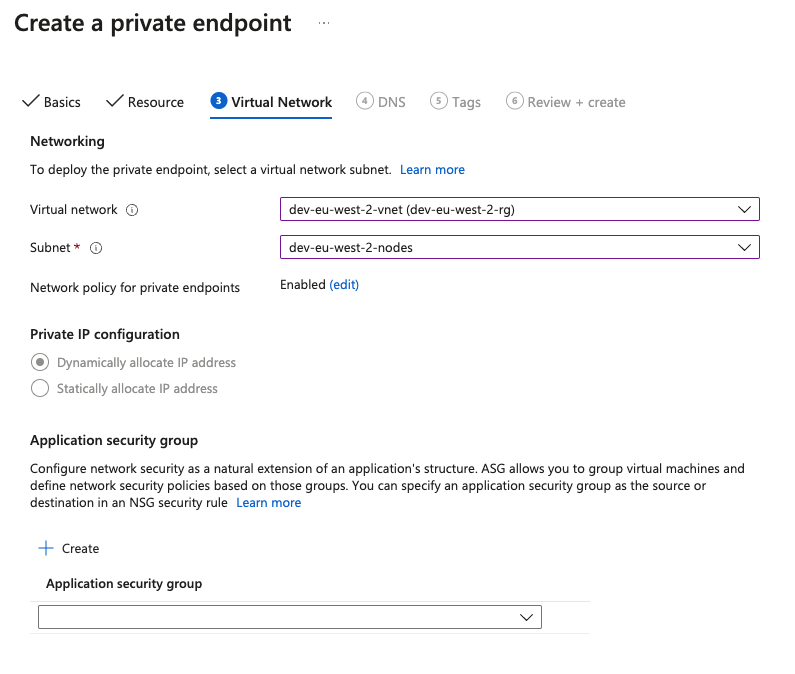
Continue to Virtual Network. Select your Virtual Network and Subnet.
![Network]()
Choose Review + Create and proceed to create the resource. The Private Endpoint is created with
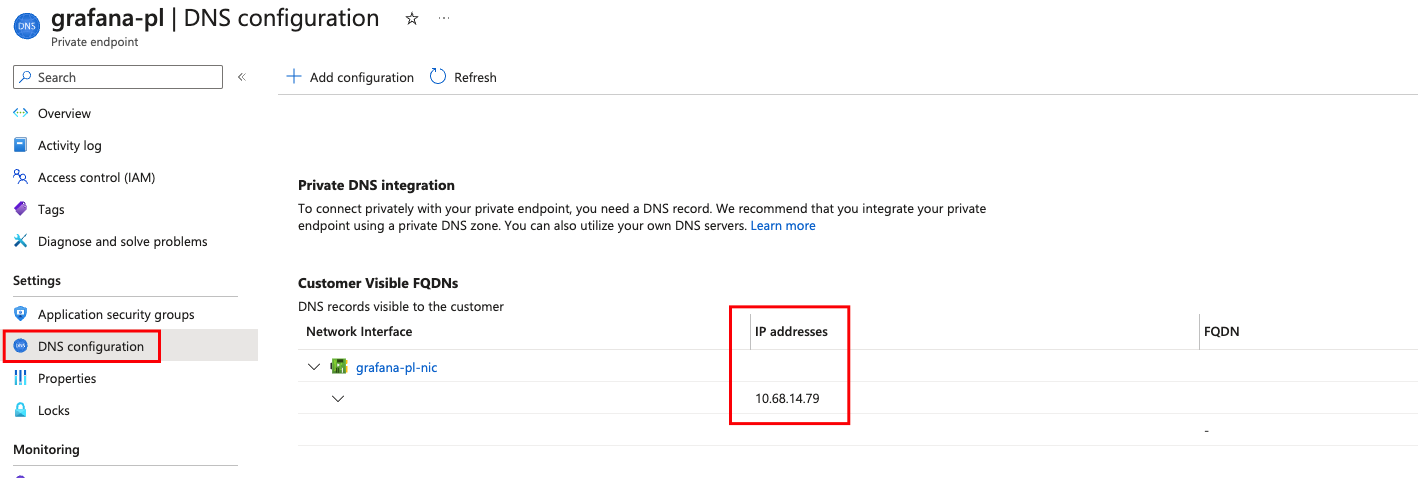
Awaiting Approvalstatus. After a maximum of 10 minutes, connection is automatically approved and status should transition toApproved. If status stays asAwaiting Approval, contact Grafana Support to request the manual approval of the connection.Under DNS Configuration, copy the local IP address of the private endpoint. You will need this IP later.
![IP Address]()
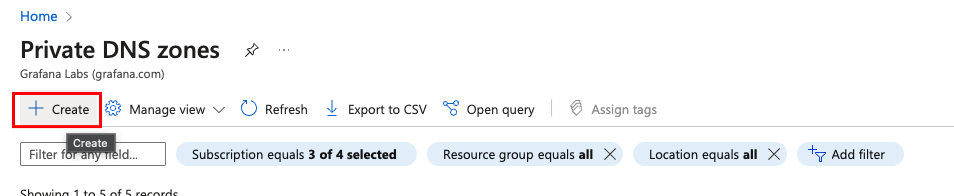
Navigate now to Private DNS zones and click on Create.
![Create DNS Zone]()
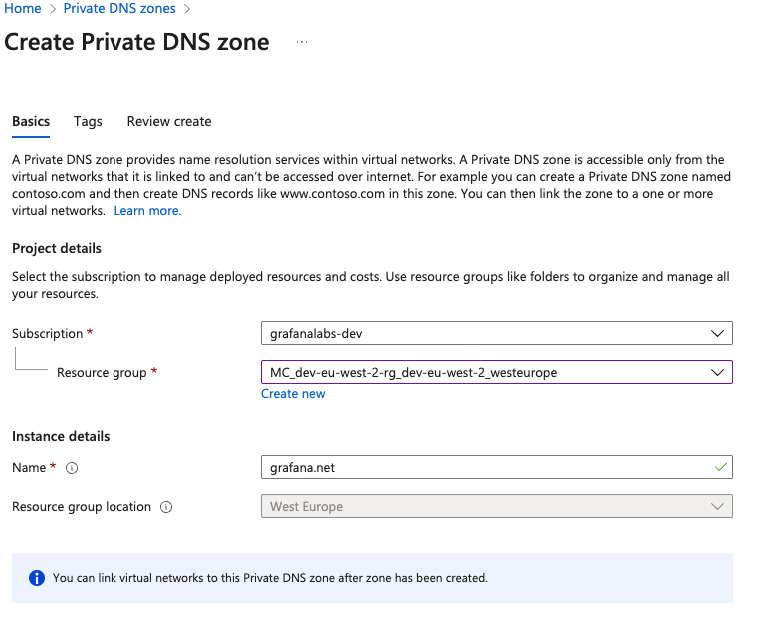
Select the subscription and resource group.
In Instance Details > Name, enter
grafana.netand then proceed to create.![DNS Zone]()
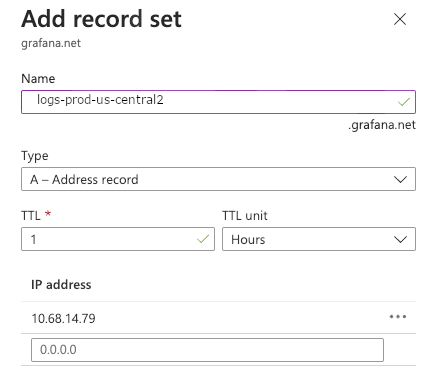
Return to Private DNS Zone overview and add a Record Set.
In Name , introduce the DNS name of the endpoint, for example
logs-prod-us-central2. Repeat this for every other endpoint you want to connect via Private Link.In IP Address, enter the local IP Address of the Private Endpoint.
![Record Set]() .
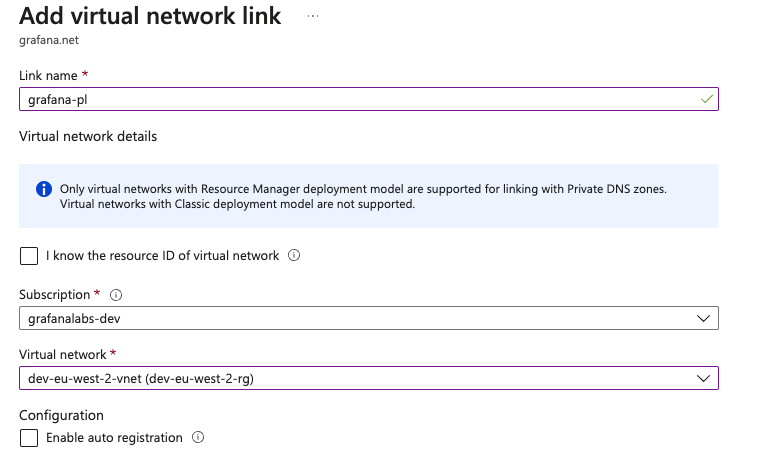
.Navigate to Virtual network links, then click on Add.
Name the network link, for example
grafana-pl.Select your subscription and Virtual Network.
![Virtual Network Link]() .
.After you create this link, all endpoints you created a DNS entry resolve to the Private Endpoint IP, so their data is sent to Grafana Cloud via Private Link.
Use Terraform
Use the following snippet to automate Private Endpoint setup in Azure using Terraform:
locals {
region = "<your azure region>"
resource_group_name = "<your resource group name>"
vnet_id = "<your virtual network id>"
subnet_id = "<your subnet id>"
privatelink_service_alias = "<private link service alias provided by Grafana>"
}
resource "azurerm_private_endpoint" "privatelink_grafana" {
name = "grafana-pl"
location = local.region
resource_group_name = local.resource_group_name
subnet_id = local.subnet_id
private_service_connection {
name = "grafana-pl"
is_manual_connection = true
request_message = "connection request from <customer grafana org name>"
private_connection_resource_alias = local.privatelink_service_alias
}
}
resource "azurerm_private_dns_zone" "privatelink_grafana" {
name = "grafana.net"
resource_group_name = local.resource_group_name
}
resource "azurerm_private_dns_zone_virtual_network_link" "privatelink_grafana" {
name = "grafana-pl"
resource_group_name = local.resource_group_name
private_dns_zone_name = azurerm_private_dns_zone.privatelink_grafana.name
virtual_network_id = local.vnet_id
}
resource "azurerm_private_dns_a_record" "privatelink_grafana_logs" {
name = "logs-prod-us-central2"
zone_name = azurerm_private_dns_zone.privatelink_grafana.name
resource_group_name = local.resource_group_name
ttl = 300
records = [azurerm_private_endpoint.privatelink_grafana.private_service_connection[0].private_ip_address]
}
resource "azurerm_private_dns_a_record" "privatelink_grafana_metrics" {
name = "prometheus-us-central2"
zone_name = azurerm_private_dns_zone.privatelink_grafana.name
resource_group_name = local.resource_group_name
ttl = 300
records = [azurerm_private_endpoint.privatelink_grafana.private_service_connection[0].private_ip_address]
}
 .
. .
.

