Configure CloudWatch metric streams
With Grafana Cloud Observability Amazon CloudWatch metric streams, you can push CloudWatch metrics using Amazon Data Firehose, providing real-time insights and scalability while simplifying configuration and reducing manual effort.
What gets created
The configuration process sets up the following components:
- Access policy token: A Grafana Cloud token with
metric:writepermissions - AWS IAM roles: Multiple roles that authorize communication among required AWS services and between AWS services and Grafana Cloud
- CloudWatch metric stream: Captures metrics from CloudWatch in real-time and puts them on a Data Firehose delivery stream
- Data Firehose delivery stream: Delivers batches of metrics to Grafana Cloud using an HTTP endpoint
- AWS resource metadata scrape job: Enriches metrics with additional metadata like resource ARNs and tags
Data flow
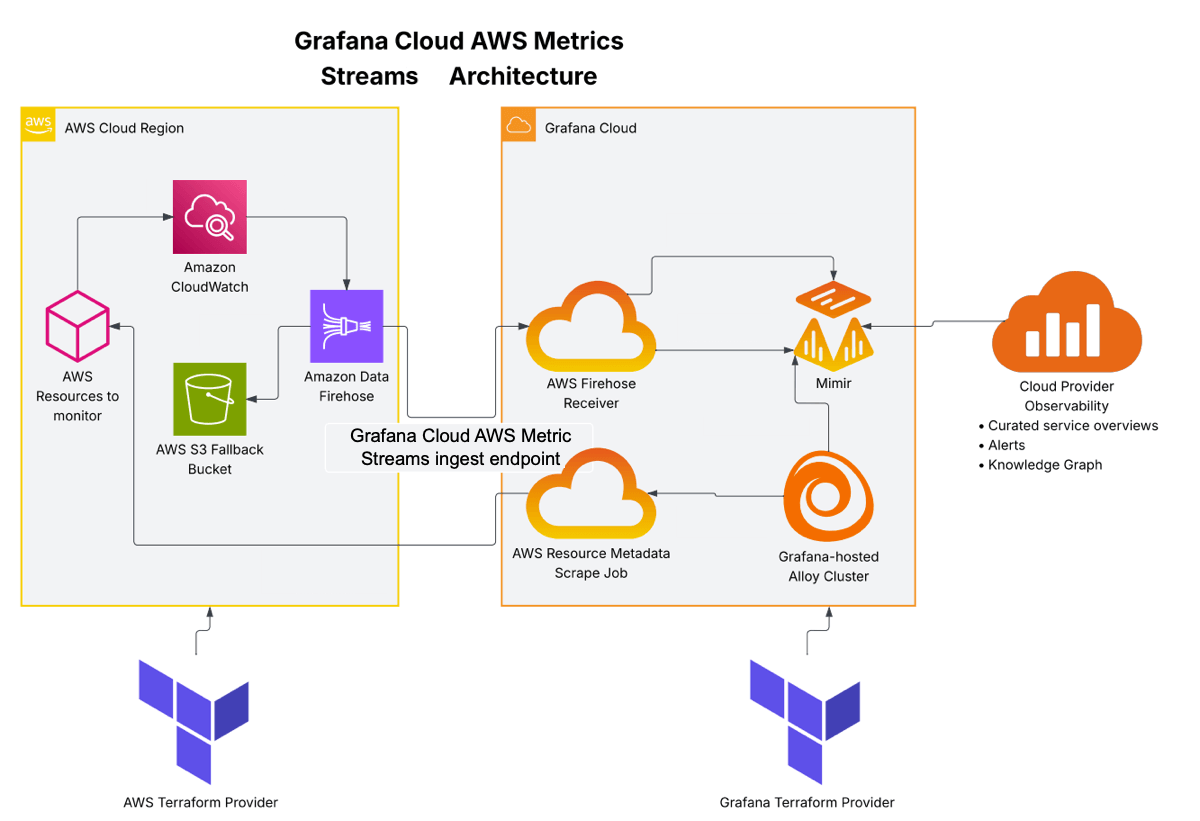
- Push raw service metrics
- Push filtered service metrics
- Backup on write failure
- Scrape tagged resource metadata as info metrics
- Collect scraped info metrics
- Write info metrics
- Read info metrics to enrich service metrics
- Write enriched service metrics
How it works
- CloudWatch continuously streams metrics to the metric stream
- The metric stream forwards data to Data Firehose in OpenTelemetry format
- Data Firehose batches and delivers metrics to your Grafana Cloud endpoint
- If delivery fails, Data Firehose backs up failed batches to S3
- The resource metadata scraper periodically fetches AWS resource tags and metadata
- Grafana Cloud combines metric stream data with resource metadata for rich context
Before you begin
Before configuring CloudWatch metric streams, ensure you have:
- AWS permissions: Sufficient access to your AWS account to manage IAM roles, CloudWatch metric streams, and Data Firehose delivery streams
- Grafana Cloud access: Sufficient access to your Grafana Cloud portal with permissions to create access policy tokens
- Configuration tool: Either AWS CloudFormation or Terraform installed and configured
- For CloudFormation: Access to the AWS account you want to monitor
- For Terraform: Terraform 1.0 or later installed locally
Note
The metric stream and Data Firehose resources must be created in each AWS region you want to monitor. The resource metadata scrape job can query multiple regions from a single configuration.
Generate an access policy token
Both CloudFormation and Terraform configuration methods require an access policy token with metric:write permissions from Grafana Cloud.
To generate an access policy token:
- Open your Grafana Cloud portal.
- Expand Observability > Cloud provider in the main menu.
- Select AWS, the Configuration tab, and the CloudWatch metric streams card.
- Enter a name for the token and click Create token.
- Copy the token value and store it securely. You’ll need it in the next steps.
Warning
The token is only displayed once. If you lose it, you must create a new token.
If you are using Terraform, store this token value in your variables or secrets management system.
Choose your configuration method
You can configure CloudWatch metric streams using either CloudFormation or Terraform. Choose the method that best fits your infrastructure management approach.
CloudFormation
Best for:
- Quick setup with minimal configuration
- Teams primarily using AWS-native tools
- Simple deployments in a single AWS account, region, and namespace
Provides:
- Pre-built template with sensible defaults
- Quick deployment via AWS Console
- Automatic resource creation and dependency management
Tip
CloudFormation is the fastest way to get started if you’re setting up metric streams for the first time or in a single account.
Configure with CloudFormation →
Terraform
Best for:
- Infrastructure as Code (IaC) workflows
- Multi-account or multi-region deployments
- Integration with existing Terraform configurations
- Version control and automated deployments
Provides:
- Full customization of all resources
- Integration with Terraform state management
- Reusable modules for multiple deployments
- Integration with CI/CD pipelines
Tip
Choose Terraform if you manage your AWS infrastructure as code or need to deploy metric streams across multiple accounts or regions.



