Authorize your service with an access policy and token
You can manage Grafana Cloud Access Policies using the API, the Access Policies page in the Cloud Portal, or the Grafana Administration settings.
To use Grafana Cloud Access Policies, you need to:
- Create an access policy
- Create one or more tokens
- Add the token to your agent or Grafana data source configuration file
For an introduction to Grafana Cloud Access Policies, read the November 22, 2022, blog post by Ryan Melendez, “Grafana Cloud Access Policies: Say hi to the new Cloud API keys.”
There’s supposed to be a video here, but for some reason there isn’t. Either we entered the id wrong (oops!), or Vimeo is down. If it’s the latter, we’d expect they’ll be back up and running soon. In the meantime, check out our blog!
Before you begin
- To manage access policies from the Grafana Administration settings, you must have the Admin role within that Grafana. However, to manage access policies in the Cloud Portal, you must have the Admin role within the Cloud Portal. These roles are set independently.
Create an access policy
Following the principle of least privilege, an access policy should only have the necessary scopes. Consider whether the access policy needs to apply to only one stack or across multiple stacks within an organization. For example, since publishing metrics is done separately from reading metrics, consider having:
- One access policy to read metrics
- One access policy to write metrics
And similarly:
- One access policy to read logs
- One access policy to write logs
Depending upon how you are setting up your access policies, you may need to create more than one access policy and token.
If the access policies need to apply to multiple stacks within an organization, then the access policy (or policies) and tokens can be created in the Access Policies page in the Cloud Portal. If the access policies and tokens only apply to one stack, then you can configure access policies within that stack’s Grafana.
To use the API, refer to the Create an access policy section of the Grafana Cloud API document.
Create an access policy for a stack
To create an access policy using Cloud access policies:
Sign in to Grafana Cloud and start the stack where you wish to create the access policy.
Click Administration in the left-side menu and select Cloud access policies.
Click Create access policy.
Enter a Display Name for the access policy.
Optional: Update the Name field. This field is automatically populated with the Display name.
Select one or more scopes for the policy. Not all scopes are displayed by default. If you do not see the scope that you are looking for, (for example,
stack:read) use the Add scope drop-down towards the bottom of the dialog, and select the scope you would like to configure.Add Label selectors, if desired. The label selectors use Prometheus labels. You can use operators like
!=and=.
Tip: Refer to Using label-based access control for additional information.Add IP ranges, if desired.
For more information, refer to Using IP range based access control with access policies.
Select Create to add the access policy.
Create an access policy for an organization
Organization-level access policies apply to all stacks within an organization unless you select specific stacks in the Realm field. To create an access policy using the organization’s Access Policies page:
Sign in to Grafana Cloud.
Select an organization in the drop-down at the top of the page.
Locate Security in the left-hand navigation and select Access Policies.
Select Create access policy.
Enter a Display Name for the access policy.
Optional: Update the Name field. This field is automatically populated with the Display name.
Optional: Select one or more stacks from the Realm drop-down. If no stack is selected, then the access policy applies across the organization.
Select one or more scopes for the policy.
Add Label selectors, if desired. The label selectors use Prometheus labels. You can use operators like
!=and=.
Tip: Refer to Using label-based access control for additional information.Add IP ranges, if desired.
For more information, refer to Using IP range based access control with access policies.
Select Create to add the access policy.
Create one or more access policy tokens
Any data source that you use with Grafana Cloud requires a token that is associated with an access policy to use in requests from that data source to a service. For example, if you create an access policy specific for reading logs, then you will need to create a token for that policy that can be added to your Loki configuration.
Note
Any token you create is only shown once. Copy and save it in a safe place, like a secure note, password app, or other protected location. If you lose a token, you will need to generate a new one and update any configurations where that token was used.
To use the API, refer to the Create a token section of the Grafana Cloud API documentation.
To create a token for an access policy:
- Sign in to Grafana Cloud.
- Navigate to the access policies page.
- From within a Grafana Stack: Click Administration and select Cloud access policies.
- Using the Cloud Portal: Select your organization, then under Security, select Access Policies.
- Choose an access policy.
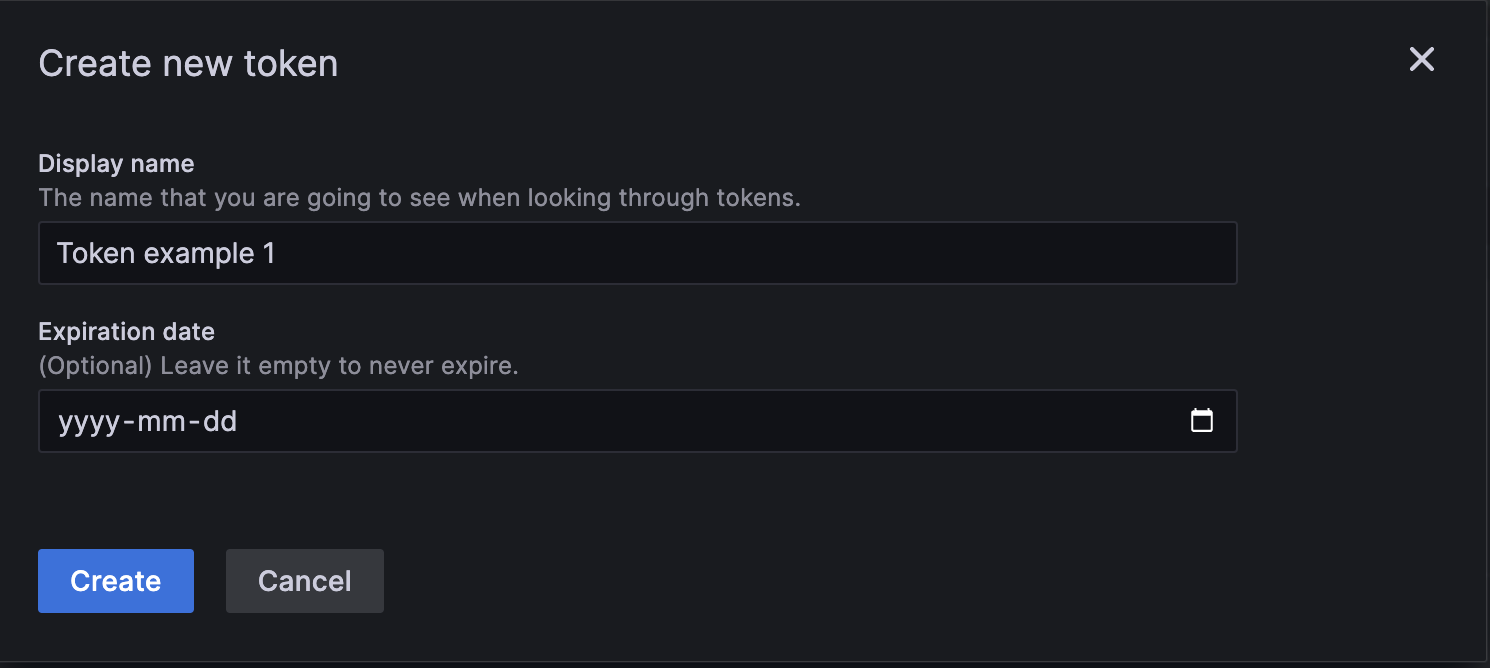
- Select Add token to display the Create new token dialog.
![Create a new token dialog Create a new token dialog]()
Create a new token dialog - Enter a Display name for the token.
- Optional: Enter an Expiration date in year/month/day format. Leave the field blank to prevent the token from expiring.
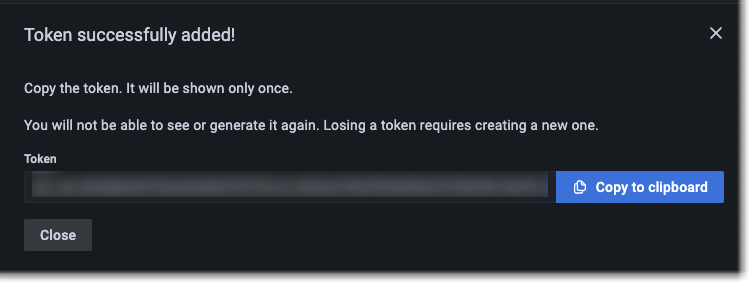
- Select Create to generate the token.
![The available scopes in the Cloud Access Policies plugin. The available scopes in the Cloud Access Policies plugin.]()
The available scopes in the Cloud Access Policies plugin. - Select Copy to clipboard to copy the generated token.
Next, either add the token to your data source’s or agent’s configuration or save the token in a secure location like a password app so you can refer to it later.
Add the token to your agent or Grafana data source configuration
The token you created needs to be added to the agent or Grafana data source configuration to allow agents to include the token with any request sent to Grafana Cloud. If the API request does an action that is allowed by an access policy (identified by the token), then the API request will be authorized.
These tokens will either be used with a data source in Grafana Cloud or with the tool that you use to send data to Grafana–most likely the Grafana Agent.
Grafana Cloud supports many integrations and data sources. The exact steps for adding the token to each integration and data source may vary. In general, agent or service configurations that reference a password or API key can be replaced with the token.
Note
Tokens do not replace user account passwords.
This procedure provides the approximate steps to create a data source using a Grafana Cloud token:
Copy the token for the service you are selecting.
In Grafana, select Connections in the left-side menu.
Filter for the data source you wish to update or add.
When you add a data source, you’ll be taken to the configuration page for it.
On the Settings tab, update the Basic Auth details for your data source. For example, if you are using Loki, then the User is the log tenant ID and the password is the token.
Select Save & test to verify the configuration.
For more detailed instructions, please refer to the integration documentation:
Note
You can see specific configuration instructions for creating data sources based on Grafana Cloud Prometheus, Loki, Graphite, Tempo, or Alert Manager by signing into your Grafana Cloud account, choosing a stack, and selecting the given service.
Modify an access policy
You can change an access policy created within a stack using the Access Policy page in the Cloud Portal. However, an access policy created in the Cloud Portal and applied to a stack can not be modified using the Cloud access policies from within the stack; the policy has to be changed at the Access Policies page.
To use the API, refer to the Access Policies endpoint section of the Grafana Cloud API documentation.
To modify an access policy:
- Sign in to Grafana Cloud.
- Navigate to the access policies page.
- From within a Grafana Stack: Click Administration and select Cloud access policies.
- Using the Cloud Portal: Select your organization, then under Security, select Access Policies.
- Locate and select the access policy you wish to modify.
- Modify the policy as desired and select Update to save the changes.
Delete an access policy token
Once a token has been created, it can not be modified. Removing the token prevents it from being used with any defined access policies.
For API instructions, refer to the Delete a token section of the Grafana Cloud API documentation.
To delete a token:
- Sign in to Grafana Cloud.
- Navigate to the access policies page.
- From within a Grafana Stack: Click Administration and select Cloud access policies.
- Using the Cloud Portal: Select your organization, then under Security, select Access Policies.
- Locate the access policy associated with the token you wish to remove.
- Select the trash can icon to the right side to remove the token.
- Confirm the removal by selecting Delete on the Delete token dialog.
Delete an access policy
Deleting an access policy removes all tokens associated with it. There may be a few minutes delay to apply everywhere.
To use the API, refer to the Access Policies endpoint section of the Grafana Cloud API documentation.
To delete an access policy:
- Sign in to Grafana Cloud.
- Navigate to the access policies page.
- From within a Grafana Stack: Click Administration and select Cloud access policies.
- Using the Cloud Portal: Select your organization, then under Security, select Access Policies.
- Locate the access policy you wish to remove.
- Select the trash can icon to the right side to remove the policy.
- Confirm the removal by selecting Delete on the dialog.
Was this page helpful?
Related resources from Grafana Labs