Important: This documentation is about an older version. It's relevant only to the release noted, many of the features and functions have been updated or replaced. Please view the current version.
Overview
GEM supports creating access policies that can span multiple tenants. Doing so enables viewers in Grafana Enterprise to view data coming from more than one tenant simultaneously. For example, if there were a tenant called team-engineering and a tenant called team-finance, an administrator might want to query metrics from both tenants simultaneously.
Prerequisites
A configured Grafana Enterprise Metrics cluster. To create a GEM cluster, refer to Set up GEM.
This guide will assume there are two tenants:
team-engineeringandteam-finance. To create a tenant, refer to Set up a GEM tenant.
Set up an access policy with tenant federation and a token
To allow queries to span both GEM tenants, which are for demonstration purposes named team-engineering and team-finance,
create a new access policy called leadership. The necessary steps are:
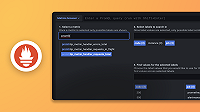
Create a new access policy
leadership.Enable the
Readscope.Add the tenants
team-engineeringandteam-finance. Alternatively, you can add the special tenant name*to create an access policy that has access to all tenants in the cluster.Create a new token for the access-policy and store the token in your clipboard:
Set up a Grafana data source using the access policy
Create a new Prometheus data source from the Grafana configuration menu.
Enter the URL of your GEM cluster, for example
http://metrics-enterprise/prometheus.From the Auth section, enable Basic auth.
In the User field, enter:
team-engineering|team-financewhere all the names of the tenants that you want to query across are separated by the|pipe character.In the Password field, paste the token created in the token creation process.
Queries that are performed using this data source in either Explore or inside of dashboards are performed across all of the tenants that you specified in the User field, and are processed as if all of the data were in a single tenant.
To submit a query across all tenants that your access policy has access to, you can either:
- Explicitly set the name of all the tenants separated by a pipe character “|” in the username. For example, to query across
tenant1,tenant2, andtenant3you would entertenant1|tenant2|tenant3. - Set the username to a wildcard character “*”. This will query all tenants that the access policy grants you access to, without requiring you to explicitly specify the their names.
When using an access policy that has a wildcard (*) as the username, you can query all tenants for that cluster by also specifying * as the username in your data source URL.
Conversely, if you use a wildcard username in your data source URL with an access policy with specific tenants, that data source has access to only those tenants.
Was this page helpful?
Related resources from Grafana Labs