Important: This documentation is about an older version. It's relevant only to the release noted, many of the features and functions have been updated or replaced. Please view the current version.
Using label-based access control
Note: This feature is available from v1.1.0. For the latest releases, refer to Download Grafana Enterprise Logs.
Label-based access control creates access policies that allow you to query only the logs that meet specific label requirements. The feature allows you to associate multiple sets of Prometheus label selectors with a policy. As a result, queries only return data from the logs that match at least one of the provided selectors. This correlates to disjunctive normal form, which allows you to express any required policy.
Setting up a label policy
Label policies are set when you create an access policy on a per-tenant basis. This means that each tenant that is associated with an access policy can have a unique label policy.
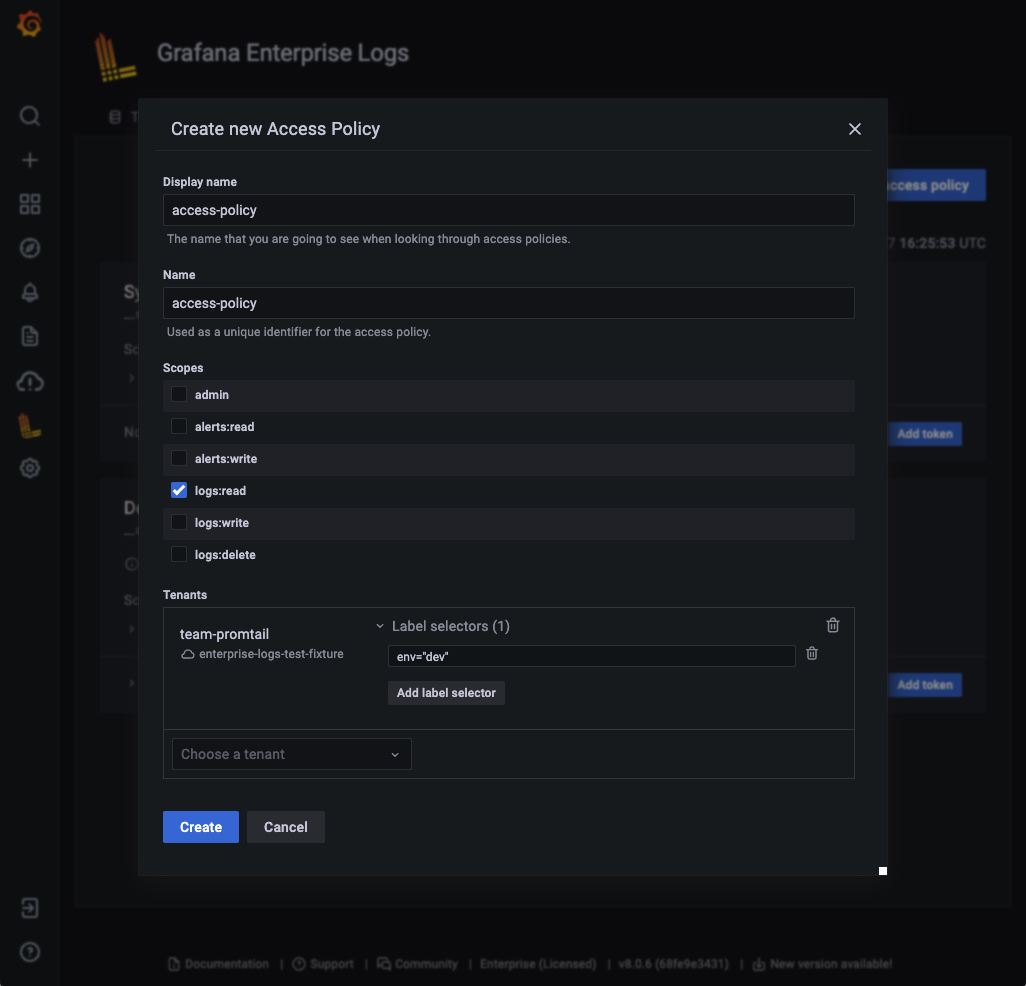
- Click the Create access policy button.
- Fill in the Display name field with the access policy name.
- Select the
logs:readscope. - Select a tenant.
- Click the Add label selector button and add a label selector.
- Click the Create button.
![Create LBAC policy Create LBAC policy]()
Create LBAC policy
Label policy scope
Label policies are only applied to the log stream selector of the Loki query. They do not apply to label filter expressions. For more information, refer to the Log stream selector and Label filter expression sections in the Loki documentation about Log queries.
Exclude a label
One common use case for creating an LBAC policy is to exclude logs that have a specific label. For example, you can create a label policy that excludes all log lines with the label secret=true by adding a selector with secret!="true" when you create an access policy:

Use multiple selectors
To create a policy that allows someone to access the production and development environments and excludes logs with the label secret=true in the production environment, use multiple selectors.

The selectors {secret!="true", env="prod"} and {env="dev"} enforce the policy:
- The selector
{secret!="true", env="prod"}matches and returns log lines from the production environment that do not have thesecret: truelabel. - The selector
{env="dev"}matches and returns log lines from the development environment, even if they have thesecret: truelabel.
Was this page helpful?
Related resources from Grafana Labs