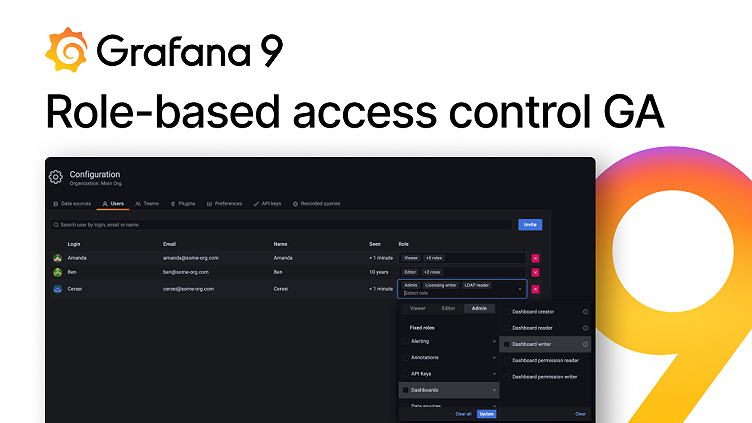
New in Grafana 9: Role-based access control (RBAC) is now GA
Role-based access control (RBAC), previously referred to as fine-grained access control (FGAC), is Grafana’s new authorization system. It was introduced as a beta feature in Grafana 8.0 release a year ago, and we’re now excited to promote it to general availability status. With the release of Grafana 9.0 during GrafanaCONline 2022, RBAC is enabled by default for all instances. (The easiest way to get started with Grafana 9? Sign up for a free Grafana Cloud account today.)
Why RBAC?
If you are running Grafana as part of a monitoring service for a large number of teams and users, you’ve probably wished you had more control over Grafana’s access setup. For example, you might have wanted to allow all Organization Editors to create reports or all members of a particular team to manage alerts. Or perhaps you have felt uneasy granting Organization Admin permissions to an API key when you only required it to access a subset of admin functionalities.
We have listened to your feedback and have been working hard this year to give you a more flexible and secure access control system so you can rest easy knowing the right people and apps can do everything they need to — and nothing they shouldn’t be.
How the Grafana RBAC feature benefits users
If you are using the open source version of Grafana, the transition from legacy access control to RBAC is seamless, and you shouldn’t notice any difference in your access setup. You can still assign viewer, editor, and admin roles to your users and service accounts, customize dashboard and folder permissions, and use teams.
As a Grafana Enterprise or Grafana Cloud user, you will also experience a seamless transition to RBAC, with all of the legacy permissions migrated over automatically.
Moreover, Grafana Enterprise and Grafana Cloud Advanced users can also use additional RBAC functionalities that allow you to fully customize the level of access that each user has for each Grafana resource currently covered by RBAC. You can assign RBAC roles like Dashboard Writer, Team Creator, or Data Source Reader to users, teams, and service accounts. You can also create custom roles by combining actions and scopes in a way that works for you. For instance, a custom role that contains teams:create permission and org.users:read permission for scopes users:id:10, users:id:11… would allow grouping a subset of users into teams.
To further manage their RBAC setup, Grafana Enterprise and Grafana Cloud Advanced users can also provision roles and role assignments through Grafana provisioning (see the example below) or Terraform; use the RBAC role picker in the Grafana UI; and use the RBAC API.
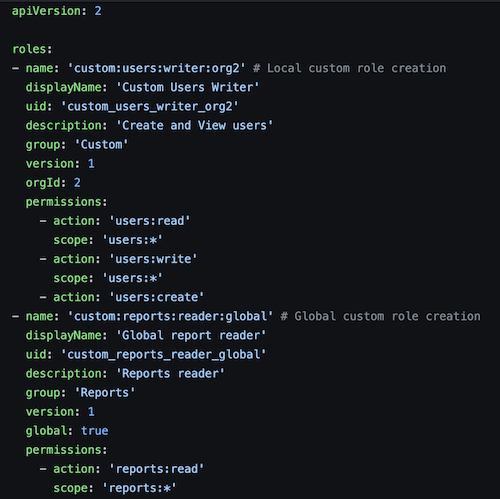
Take a look at our guide on planning your RBAC rollout strategy to learn more about how to make the most of RBAC.
Improvements to RBAC in Grafana 9.0
- Extended resource coverage - All of the main Grafana resources are now covered by RBAC, including dashboards, folders, users, teams, and data sources. We have created handy reader and writer roles for these resources, and you can also define your own custom roles. Our documentation contains a full list of resources covered by RBAC and RBAC role definitions.
- Role assignments to users, teams, and service accounts - You can now assign roles directly to users, teams, and service accounts. This gives you full control over what each user is authorized to do, while providing a simple way to manage permissions for a group of users or an integrated application like Terraform.
- Audit logs for RBAC - Any calls to RBAC endpoints are now registered in audit logs, so you have a record of permission changes and who has carried them out.
- Thoroughly tested - RBAC has been used in production on large-scale installations of Grafana throughout the year to make sure that this transition is as safe and convenient as possible.
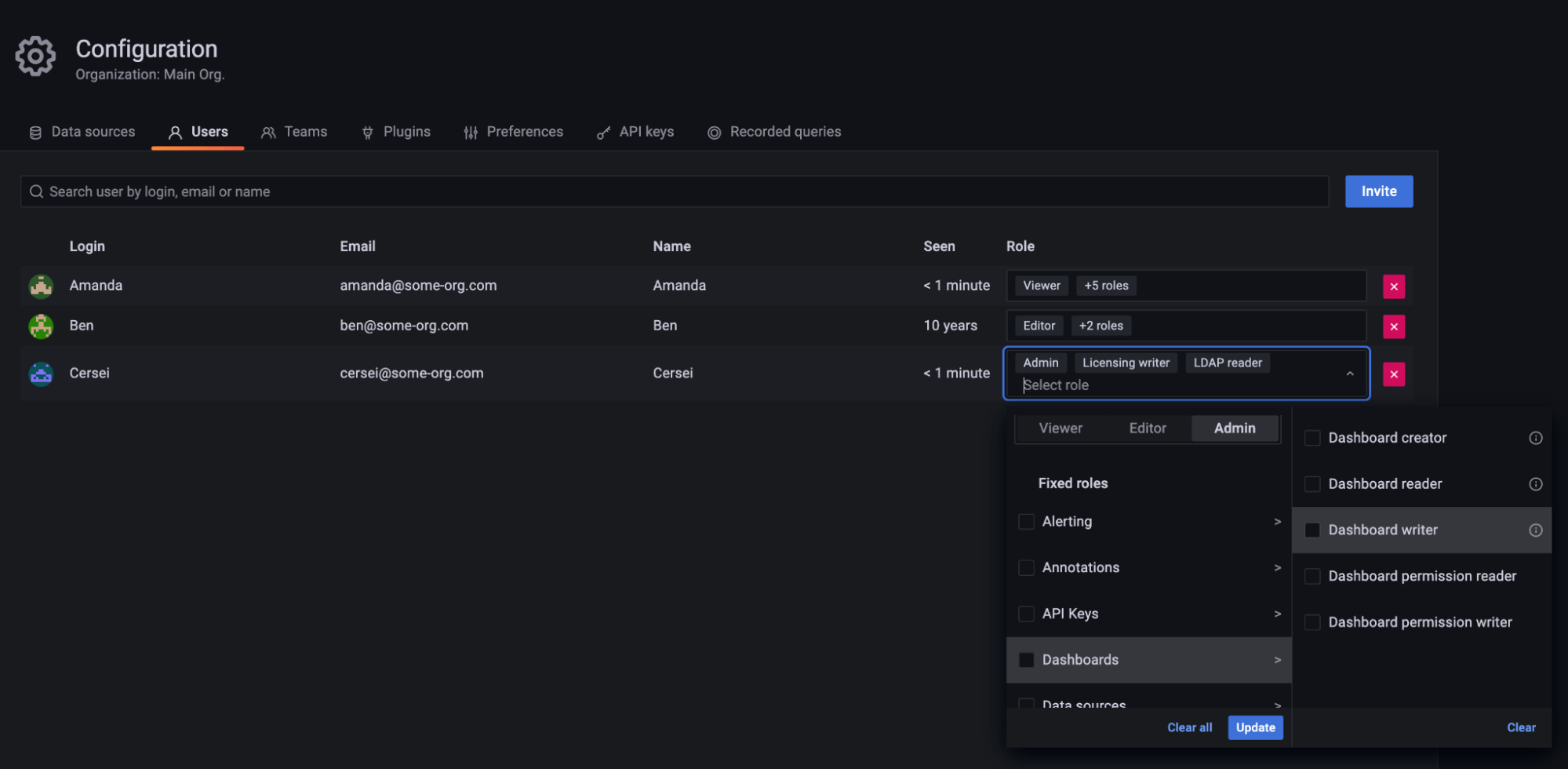
- Role picker - You can now view and manage user, team, and service account role assignments directly from Grafana’s UI, as illustrated in the screenshot below. Follow our guide to learn how to assign roles using the role picker.
Breaking changes
The Grafana 9.0 release contains several breaking changes for RBAC:
- Built-in roles are now called basic roles, and they now consist of permissions, not roles.
- The Terraform builtin_role_assignment resource is going away.
- Basic roles no longer support permission inheritance. Previously, when permissions of a Viewer basic role were modified, it was propagated to the Editor and Admin basic roles. This is not the case anymore. For example, if you want to grant Viewers and Editors edit permissions over a dashboard, you’ll need to assign this permission to both basic roles instead of only the viewer role.
- Grafana provisioning has a new schema, please refer to the Grafana documentation for more information.
- Several RBAC actions have been renamed to increase action name consistency. We have provided migrations for all the database entries that use legacy action names, but provisioning files and scripts will have to be updated by the user. This change also means that if Grafana is downgraded from 9.0 to a lower version, some RBAC permissions will not be correctly resolved.
What’s next for RBAC in Grafana?
We have an exciting roadmap full of RBAC improvements in Grafana. Here is a preview of what’s to come:
- RBAC for app plugins - Our next step is to facilitate controlling access to Grafana Cloud plugins like Grafana OnCall and Synthetic Monitoring with RBAC.
- Simplify the user, team, and service account creation flow - The current resource creation flow is a multi-step process: You first need to create the resource and then assign roles to it. We want to make this workflow smoother by presenting the role picker when you create a user.
- Simplify scoping - We want to make it easier to scope permissions to a group of entities like data sources, service accounts, and reports. This will involve thinking about ways of grouping entities, similar to what folders currently provide for dashboards and teams provide for users, and then expanding our implementation of scopes.
- RBAC role sync - We want to allow Grafana Enterprise and Grafana Cloud Advanced users to map roles from external auth providers to RBAC roles, similar to the current role mapping for Grafana’s Viewer, Editor, and Admin roles.
You can discover more about RBAC in Grafana 9 in our Grafana documentation. We hope you enjoy exploring RBAC and find it useful! Get in touch with us for any questions, feedback or issues related to RBAC on our Grafana Labs Community Slack or through GitHub.
Grafana Cloud is the easiest way to get started with Grafana 9. We have a generous free forever tier and plans for every use case. Sign up for free now!